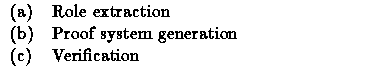
Starting from a protocol description, the algorithm operates in three main steps:
In the sequel, we will motivate, explain and illustrate each of these three steps. The illustration will be carried out on the Woo and Lam authentication protocol.